Preventing insider threats
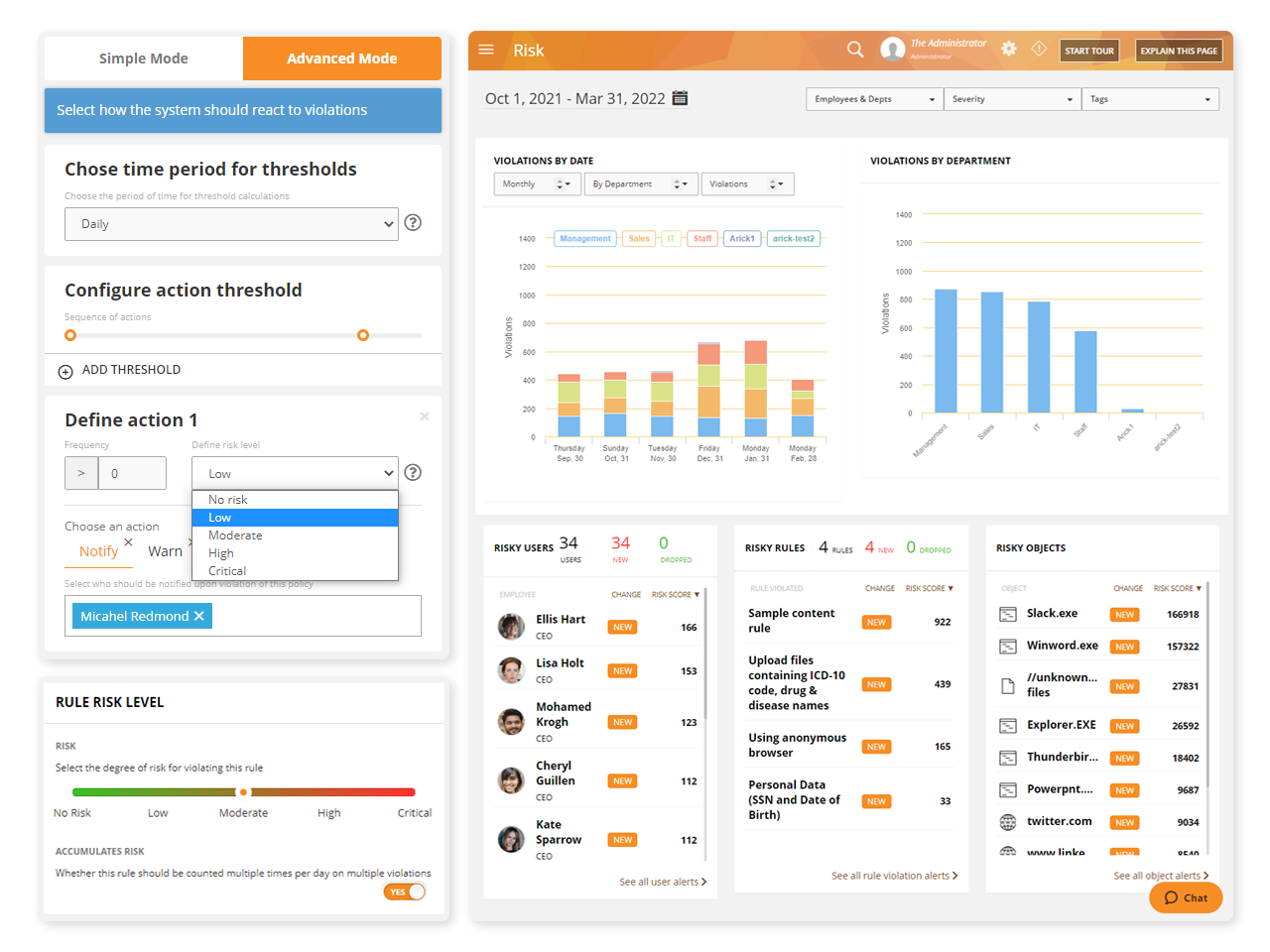
No business, enterprise or SME is immune to insider threats. To detect and prevent them, organizations need proactive and modern solutions that complement traditional cybersecurity tools.
Teramind’s analytics, automated incident response, and contextual user monitoring data strengthen cybersecurity and provide security teams with rich data to identify malicious insiders.